Tech
Key Features to Look for in an Identity and Access Management System
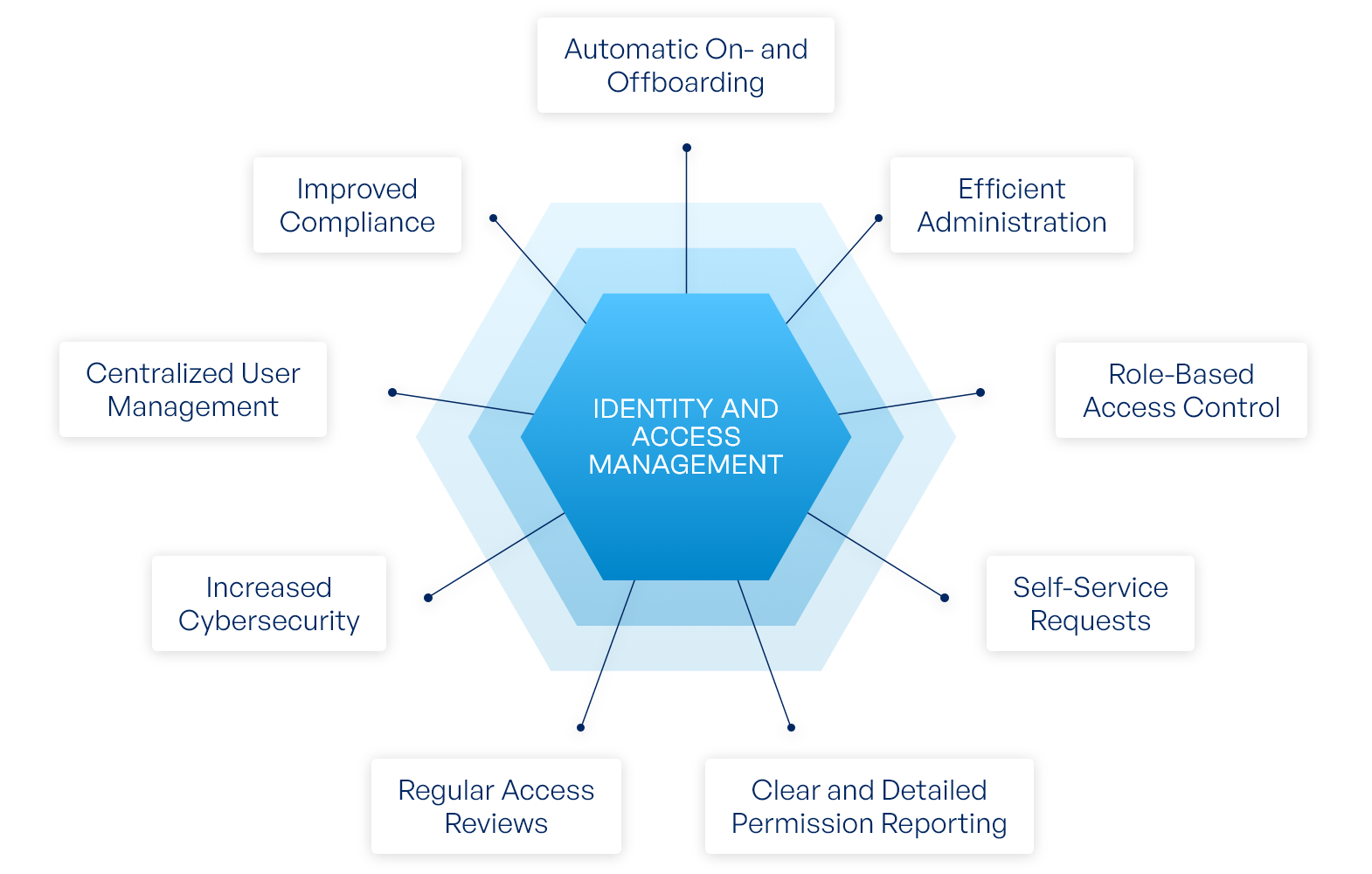
Key Takeaways:
- Identity and Access Management (IAM) is essential for managing and safeguarding user identities.
- A robust IAM system must offer various authentication and authorization options to adapt to security needs.
- User life cycle management, access governance, and compliance are intrinsic to maintaining data integrity and meeting regulatory standards.
- SSO and MFA greatly enhance security and user experience.
- Biometric authentication and identity federation are indicative of future advancements in IAM technologies.
Introduction to Identity and Access Management (IAM)
Identity and Access Management (IAM) systems ensure appropriate access controls across an organization’s digital landscape. As security threats escalate and compliance requirements become more stringent, selecting an IAM system that embodies the right features is increasingly vital. This system is the gatekeeper of digital identities and enables efficient business processes, offering superior user experiences.
With the continual evolution of security protocols, IAM solutions play a pivotal role in managing digital identities, supporting workflow efficiency, and bolstering the overall cybersecurity framework of organizations across various industries.
Robust Authentication Methods
In the realm of IAM, authentication stands as a fundamental component. The diversity of authentication methods available within an IAM system must reflect the modern security landscape. Beyond traditional password systems, there are now biometrics, hardware tokens, software-based authenticators, and adaptive authentication based on user behavior and risk profiles.
Such a range of available methods empowers organizations to implement security measures that match the sensitivity and risk associated with different types of data and access scenarios, ensuring the integrity of digital identities within their networks.
Comprehensive Authorization Capabilities
Authorization within IAM allows for the precise governance of user permissions. An IAM system should facilitate intricate control over these permissions, enabling administrators to granularly allocate and regulate what resources a user can access after being authenticated.
Configuring permissions at a detailed level is essential for internal security and compliance with various industry regulations. It is not only about overseeing who can access what but also what operations they can perform with that access, playing a critical role in protecting and managing sensitive data.
User Life Cycle Management Facilities
User lifecycle management within an IAM system addresses the end-to-end administration of a user’s engagement with an organization. From the moment a user’s account is created, through any role transitions, to its eventual termination, lifecycle management ensures that access rights and user identities are appropriately managed.
Automating such processes within an IAM can reduce manual workloads and mitigate the risk of oversights or errors that could leave systems vulnerable.
Access Governance and Compliance Features
Access governance embedded in an IAM system involves monitoring and enforcing compliance with established access policies and regulations. Such features support organizations in maintaining data integrity and navigating the complexities of legal compliance within an increasingly regulated digital environment.
An IAM with access governance can provide the tools necessary to carry out regular audit trails, manage segregation of duties, and keep track of access rights, thus ensuring alignment with various compliance frameworks.
Single Sign-On (SSO) Convenience
Single Sign-On (SSO) enables users to authenticate once and gain access to a suite of applications without the need to log in separately into each one. By providing SSO capabilities, an IAM system significantly simplifies the login process for users and reduces the burden of password management.
From a security standpoint, SSO can also minimize the attack surface, reducing the number of attack vectors that might be exploited through user credentials. SSO can also lead to increased productivity and a better overall user experience.
Multi-Factor Authentication (MFA)
Multi-factor authentication (MFA) adds notable strength to an IAM system by introducing additional layers of security, often crucial for access to especially sensitive systems and data. MFA significantly complicates unauthorized attempts to breach a system by demanding more than one verification form.
An IAM solution that effectively integrates MFA will present a robust and adaptive security tool that can be adjusted according to the relative risk of the access point.
Biometric Authentication Options
Biometric authentication utilizes unique biological characteristics as a security measure, offering enhanced protection. An IAM system employing biometric capabilities such as fingerprint or facial recognition increases security by binding access to the innate characteristics of the user.
Implementing biometrics within IAM frameworks strengthens security and facilitates a more user-friendly experience by providing a simple and efficient method for verifying identity.
Identity Federation Support
Identity federation represents a sophisticated IAM feature that extends identity management capabilities across different systems and domains. It allows users to authenticate once and access a network of resources without managing multiple sets of credentials.
For organizations that collaborate with a spectrum of partners and services, an IAM system with an identity federation is invaluable. It simplifies access management while maintaining strict security and privacy controls across diverse IT environments.
The Future of IAM and Ongoing Innovation
As the digital landscape continues its rapid growth and evolution, IAM systems must adapt to integrate emerging technologies that enhance security capabilities. Incorporating forward-thinking features such as AI-driven authentication methods or utilizing blockchain for decentralized identity management can place an IAM system at the cutting edge of security innovation.
Proactively seeking solutions that adapt to the future’s uncertain demands will be key for enterprises looking to maintain robust yet flexible security infrastructures in the digital age.
Tech
IP2 Network: Revolutionizing Online Streaming and Real-Time Interaction

In a digital world where content is king and live interaction reigns supreme, IP2 Network has emerged as a unique hub for real-time live streaming. Often associated with a controversial, raw, and unfiltered style of broadcasting, the IP2 Network has built a strong following by offering viewers an alternative to heavily moderated or censored content. It has carved its own niche in the online entertainment ecosystem, attracting both fans and critics.
What Is IP2 Network?
IP2 Network is a decentralized streaming and aggregation platform primarily known for hosting and indexing live IRL (In Real Life) streamers. Unlike mainstream platforms that have strict rules and guidelines, IP2 Network prides itself on freedom of expression and independent content curation. The site doesn’t host streams directly but aggregates them from platforms like YouTube, Kick, and Rumble—allowing viewers to monitor a variety of streamers in real-time.
How It Works
IP2 Network functions as a livestream aggregator and community bulletin board, automatically updating and categorizing ongoing streams. Key features include:
- Live Stream Listings: Constantly updated list of streamers who are live.
- Community Voting System: Users can upvote or downvote streams based on entertainment value.
- Chat & Forums: Some versions of the site include public chat or discussion sections for community interaction.
- Drama and Highlights: Clips and summaries of notable events are often posted for discussion.
Popular Streamers on IP2
While IP2 Network is dynamic and its featured streamers often change, it became known for supporting certain figures during the golden era of IRL streaming on platforms like Twitch and YouTube. These streamers gained traction for their unconventional, often chaotic approach to live content. Notable examples include:
- Ice Poseidon – Often referred to as the “godfather of IRL streaming,” his influence helped shape the early days of IP2.
- Captain Content
- Chicken Andy
- Attila & Jewel
These streamers are known for traveling, interacting with strangers, and sometimes getting into controversial situations, which are part of what has drawn an audience to IP2.
Why IP2 Network Is Popular
Several factors contribute to the popularity of IP2 Network:
1. Unfiltered Content
Unlike heavily moderated platforms, IP2 offers viewers raw and unedited real-life experiences.
2. Drama and Realism
The unpredictable nature of IRL streaming means that anything can happen. From dramatic confrontations to heartfelt moments, viewers are hooked by the spontaneity.
3. Community Culture
The IP2 community thrives on memes, inside jokes, and commentary. The chat culture and user interaction drive engagement.
4. Freedom from Platform Rules
Because IP2 does not host content directly, it provides a space where streamers who are banned or restricted elsewhere can still reach an audience.
Controversies and Criticism
IP2 Network is not without its share of controversies. Some critics argue that the content promoted on the platform can be toxic, problematic, or even dangerous. Issues include:
- Harassment and Doxxing: Some streamers or viewers have been accused of engaging in or encouraging inappropriate behavior.
- Platform Bans: Several streamers featured on IP2 have been banned from Twitch, YouTube, and other platforms due to terms of service violations.
- Legal Issues: Public disturbances or illegal activities caught on stream have led to law enforcement involvement in certain cases.
Is IP2 Network Legal?
The IP2 Network itself is not illegal, as it merely aggregates publicly available streams and does not host the content. However, the legality of the content itself depends on the actions of individual streamers and the platforms they use.
The Future of IP2 Network
As platforms like Kick and Rumble continue to grow, IP2 may evolve and adapt, hosting newer faces and maintaining its relevance in the ever-changing live streaming landscape. It remains a controversial yet undeniably influential force in the world of independent digital broadcasting.
Conclusion
The IP2 Network represents a counterculture movement in online streaming—unfiltered, chaotic, and sometimes problematic. For fans, it’s a source of nonstop entertainment; for critics, it’s a symbol of what happens when moderation is absent. Whether you admire its rawness or question its ethics, IP2 Network remains a fascinating case study in modern internet culture.
Tech
LeahRoseVIP: Digital Community of Professionals

In today’s fast-paced digital world,networking and professional growth are essential for success. LeahRoseVIP has emerged as a premier online community designed to connect professionals, entrepreneurs, and creatives, fostering collaboration, mentorship, and business growth.
What is LeahRoseVIP?
LeahRoseVIP is an exclusive digital community that brings together like-minded professionals from various industries. Founded by Leah Rose, a visionary entrepreneur and business strategist, this platform offers a space for members to network, share insights, and access valuable resources to elevate their careers and businesses.
Key Features of LeahRoseVIP
1. Networking Opportunities
LeahRoseVIP provides a dynamic environment where professionals can connect, exchange ideas, and build meaningful relationships. Whether you’re an entrepreneur, freelancer, or corporate professional, the community offers opportunities to expand your network.
2. Expert-Led Workshops & Masterclasses
Members gain access to exclusive workshops, webinars, and training sessions led by industry experts. Topics range from business development and branding to digital marketing and financial literacy.
3. Collaborative Projects & Partnerships
The community encourages collaboration, allowing members to team up on projects, share resources, and even form business partnerships.
4. Supportive & Empowering Environment
LeahRoseVIP is more than just a networking group—it’s a support system. Members receive encouragement, accountability, and mentorship to help them overcome challenges and achieve their goals.
5. Exclusive Digital Resources
From business templates to e-books and industry reports, LeahRoseVIP provides valuable tools to help professionals stay ahead in their fields.
Who Should Join LeahRoseVIP?
- Entrepreneurs & Business Owners looking to scale their ventures
- Freelancers & Creatives seeking collaboration and exposure
- Corporate Professionals aiming to expand their influence
- Students & Aspiring Professionals eager to learn from industry leaders
Why Join LeahRoseVIP?
In a competitive digital landscape, having a strong professional network is invaluable. LeahRoseVIP offers a curated space where ambition meets opportunity. Members not only gain knowledge but also find a tribe that supports their growth.
Final Thoughts
LeahRoseVIP is more than just a digital community—it’s a movement. By fostering connections, education, and empowerment, it helps professionals thrive in an ever-evolving market.
Tech
Hitlmila: Exploring the Emerging Digital Term and Its Potential Influence

In the ever-evolving world of the internet, Hitlmila new terms and digital trends often appear and spark curiosity. One such term gaining attention is “Hitlmila.” While not widely recognized in mainstream discourse, “Hitlmila” is gradually making its way into niche digital spaces. Whether it refers to a platform, a concept, or a coined identity, understanding its potential implications is important for staying ahead of digital culture.
What is Hitlmila?
At present, Hitlmila does not appear to have a standardized or universally accepted definition. However, based on contextual usage across various forums, speculative digital communities, and low-key platforms, “Hitlmila” could represent:
- A coded name or digital handle within gaming, tech, or underground internet culture.
- An acronym or stylized word used in creative writing, virtual storytelling, or content encryption.
- A new tech project or app that’s yet to be fully launched or promoted.
- A fictional character or narrative within web-based literature or speculative fiction.
In the digital world, such ambiguous terms often hold hidden meanings or serve as placeholders for developing ideas, projects, or identities.
Possible Origins of the Term
The origin of Hitlmila remains unclear, which adds to its intrigue. It could be:
- A blended word formed by combining meaningful syllables from different languages or cultures.
- A phantom brand or ARG (alternate reality game) name used to initiate curiosity.
- A social media pseudonym meant to stand out or break from algorithmic patterns.
Names like these are often deliberately cryptic to generate engagement and spark exploration, especially within Gen Z and millennial internet communities.
Hitlmila in Digital Culture
Terms like Hitlmila often gain traction when:
- Digital creators adopt them as usernames or product tags.
- Underground tech communities use them for early-stage projects.
- Memes or digital artwork begin associating them with specific aesthetics or concepts.
With the speed of internet trends, a name like Hitlmila could quickly evolve into:
- A recognizable brand identity in gaming, digital art, or tech tools.
- A symbol in fandom culture tied to characters or fan fiction.
- A token or domain name in the blockchain or NFT space.
The Future of Hitlmila
Whether “Hitlmila” grows into a defined entity or remains a mysterious digital artifact depends on community adoption and creative expansion. With increased user interaction, content creation, or entrepreneurial application, this term could turn into a viral brand, niche meme, or subcultural term.
Final Thought
The digital world thrives on curiosity, reinvention, and identity — and Hitlmila encapsulates all three. As the internet continues to blend creativity with technology, enigmatic terms like Hitlmila remind us of how quickly meaning can be shaped by community interaction. Stay tuned — today’s unknown word might be tomorrow’s trending brand.
-

 Tech1 year ago
Tech1 year agoUnderstanding ПРЕВОДЕЧ: Unlocking Global Communication
-

 Tech1 year ago
Tech1 year agoGeekzilla.tech Honor Magic 5 Pro: Unveiling the Technological Marvel
-

 Blog1 year ago
Blog1 year agoGeekzilla Autos: Everything You Need To Know
-

 Blog1 year ago
Blog1 year agoGeekzilla Podcast: A Journey into Geek Culture
-

 Health1 year ago
Health1 year agoWellhealth how to build muscle Tag: Complete Guide
-

 Health1 year ago
Health1 year agoWellHealthOrganic Buffalo Milk Tag: Your Nutrient-Rich Dairy Upgrade
-

 Blog1 year ago
Blog1 year agoTips for Breaking Into the Restaurant Industry
-

 Tech1 year ago
Tech1 year agoPikruos is a Leading Provider of Innovative IT Solutions
